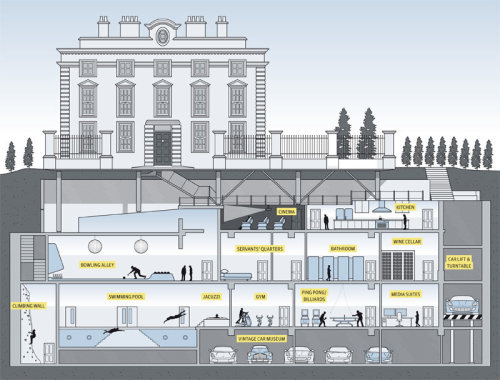
Billionaires' Basements: the luxury bunkers making holes in London streets. A new billionaires’ craze for building elaborate subterranean
extensions is making swiss cheese of London’s poshest streets – but at
what cost?
Entertainment
Every Gesture Used to Beat
Angry Birds Visualized on Paper
Instant Google Street View. Type something (slowly) and teleport around the world.
Nuclear Power Plant Simulation Game
Taliban accidentally CCs everybody on its mailing list
Internet
Google and Bing autocomplete what they think they know what you're
thinking. Sometimes they get
it wrong.
"People who study online behavior also say the autocomplete feature
reveals broader patterns, including indications that the questions
people ask of search engines often veer into the sensitive and
politically incorrect." There's even a Tumblr devoted to
Google Poetics.
In an attempt to make itself less desirable to copyright infringers, starting November 27,
RapidShare will begin capping non-paying users
at 1 gigabyte of outbound downloads per day. (Paying users will have 30
gigabytes.) Meanwhile, controversial Megaupload founder Kim Dotcom is
planning a January debut for his new
Mega
service - which plans to insure itself against litigation by having all
hosted material encrypted by the uploader's browser before
transmission.
What does proper authorization to access a computer system mean? Robert Graham of Errata Security writes about the recent conviction of
Andrew Auernheimer (aka weev) for “hacking” AT&T. Two years ago, weev discovered a
bug
in AT&T's website that exposed the email addresses of customers
with iPads. According to weev, the flaw was reported as per responsible
disclosure practices by first informing AT&T before bringing it
public. However the FBI investigated and arrested him under the Computer
Fraud and Abuse Act (CFAA). On 20th November 2012, he was
found guilty of identity fraud and conspiracy to access a computer without authorization.
Reading & Discussion
Mr. Fix-It:
The engineering mentality
What does proper authorization to access a computer system mean? Robert Graham of Errata Security writes about the recent conviction of
Andrew Auernheimer (aka weev) for “hacking” AT&T. Two years ago, weev discovered a
bug
in AT&T's website that exposed the email addresses of customers
with iPads. According to weev, the flaw was reported as per responsible
disclosure practices by first informing AT&T before bringing it
public. However the FBI investigated and arrested him under the Computer
Fraud and Abuse Act (CFAA). On 20th November 2012, he was
found guilty of identity fraud and conspiracy to access a computer without authorization.
Resources & Utilities
Responsify is a browser based tool, which allows you to create your own
responsive template. Think of it as a foundation for you to build upon.
You can customise the grid to suit your content, rather than trying to
make the content fit the grid.
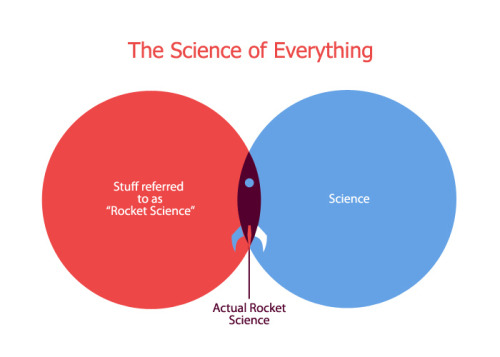
Science
David Brin points to
Asteroid belts at just the right place are friendly to life -November 6, 2012
, saying "This combination is calculated to be rare, in perhaps just
4% of solar systems. That rarity offers yet one more new, rather
daunting candidate for the Fermi Paradox."
XKCD explains explains the major parts of
the Saturn V rocket.
Software
The Frightening Things You Hear at a Black Hat Conference
Technology
Five years ago today Jeff Bezos’ Amazon.com released the
Amazon Kindle,
a move that would revolutionize the publishing industry. While often
controversial, most recently for its
international tax avoidance schemes,
Amazon has been very successful and has made millions for its founder.
What has Bezos done with some of his tax-free millions? Well for one,
he launched and landed a rocket vertically.